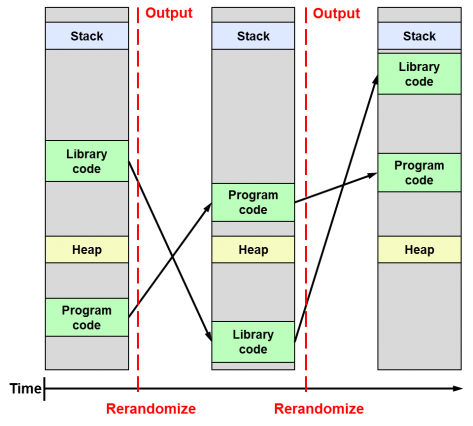
Following the release of the Linux Kernel 4.12, which for the first time brings the KASLR feature enabled by default, and almost simultaneously the announcement of a feature called KARL in OpenBSD, I found it interesting to clarify the differences between these security techniques, since I think that the combination of both will be very important in the future of system security as they will prevent exploiting vulnerabilities related to memory corruption (buffer-overflow).
How to create a Sentilo AWS EC2 instance from an OVA file
Sentilo is an open source software designed by openTrends for the exchange and processing of information from thousands of sensors and actuators, acting as an interface between them and the various applications that want to collect and make use of the information they provide. Thus, it fits well within the Smart City architecture and has the city of Barcelona as the main promoter. But Sentilo is not only made by and for the cities, but also for any organization that wants to implement an IoT application that requires deploying a smaller number of sensors and actuators, such as inside buildings or in the open field.
In this article I will detail how to deploy a Sentilo 1.6 server in a Cloud Computing environment such as Amazon Web Services by creating an EC2 instance from an AMI that will be created by importing an image in Open Virtual Appliance (OVA) format which can be downloaded from Sentilo’s website at https://www.sentilo.io/xwiki/bin/view/Sentilo.Community.Documentation/Use+a+Virtual+Machine.
How to exclude your own [dynamic] ip from Google Analytics
In my 5 ways to exclude your own visits from Google Analytics post I discussed the 5 main methods that exist to prevent visits you make to your own websites are tracked by Google Analytics, each with its pros and cons. However, I found it necessary to further expand the first of those methods, which in my opinion is the best possible way to exclude your own internal traffic from Google Analytics based on your IP address, whether fixed or dynamic. It allows you not only to block yourself but also filter the activity of all members on your own team or company, which is of utmost importance to avoid any interference with data collected from real user activity.
And I say Google Analytics because it is the main actor in this market, but this same method is perfectly suitable for any other web analytics tool like Piwik, Clicky, OWA, Clicktale, StatCounter, Kissmetrics, Mouseflow and many others.
How to prevent the .xsession-errors file from growing to a huge size
The .xsession-errors file is where the X Window system logs all errors that occur within the Linux graphical environment. All desktop environments, whether Gnome, KDE, Cinnamon, XFCE, LXDE, etc., and all lighter window managers like FVWM, IceWM or Window Maker make use of the X Window system. Therefore any graphical application running on your computer can cause that error messages are written to the .xsession-errors file, reason why it can grow wildly until reaching very big sizes of tens of GB or even hundreds if your disk capacity allows it.
Fatrace command: how to know in real time which processes are writing to a file
It is usually easy to know which process or processes are writing to a given file in Linux, since we either know its origin and its nature beforehand (for example the Apache access_log), or we can easily find it out with the fuser or lsof commands. However, sometimes it will happen that although we know the role and purpose of a file, there are so many applications accesing it simultaneously that it is very difficult to know which of them is the one that reads/writes the most or does so in a precise moment. Knowing this would be very useful to learn for example why a log file is growing excessively or which application is making an abusive use of system resources, either by mistake or intentionally.
Automatically lock/unlock your screen by Bluetooth device proximity
One of the most basic and common security measures that you can adopt in your working environment is to protect your computer by automatically locking the screen after a certain period of inactivity, so that it is necessary to enter a password to unlock. But there is a more effective way, and that is to configure your Linux machine so that the distance or proximity of a Bluetooth device you own, for example your cell phone or a smartwatch, automatically causes locking or unlocking the screen without having to enter any password on keyboard.
Use GMail with your own domain for free thanks to Amazon SES & Lambda
One of the main needs of a small business or startup is to have a reliable mail system with its own domain that helps differentiate on the Internet. Although there are lots of hosting plans offering free email accounts and even you could set up your own mail server, you are probably already used to mail services like GMail and would like to continue using it to also manage mail from your own domain without having to come to paid solutions such as G Suite (formerly Google Apps), which though inexpensive for the services you get in return, they represent an additional cost that your incipient project might not afford.
If this is your case you will be happy to know that thanks to the free tier offered by Amazon Web Services (AWS) in some of its services such as Amazon SES and Lambda, you can build a mail system at no cost that integrates seamlessly with your GMail free account, and at the same time allows you to send and receive mail from multiple mailboxes within your own domain.
ᐈ How to create a user in MySQL/MariaDB and grant permissions on a specific database


![How to exclude your own [dynamic] ip from Google Analytics](https://cdn.daniloaz.com/wp-content/uploads/2017/06/page-analytics-chrome-extension.jpg)